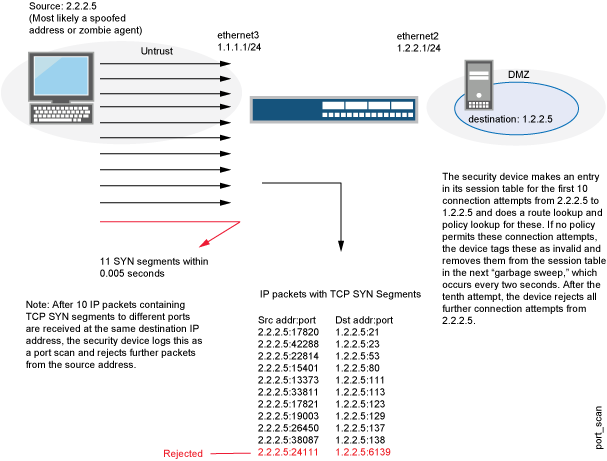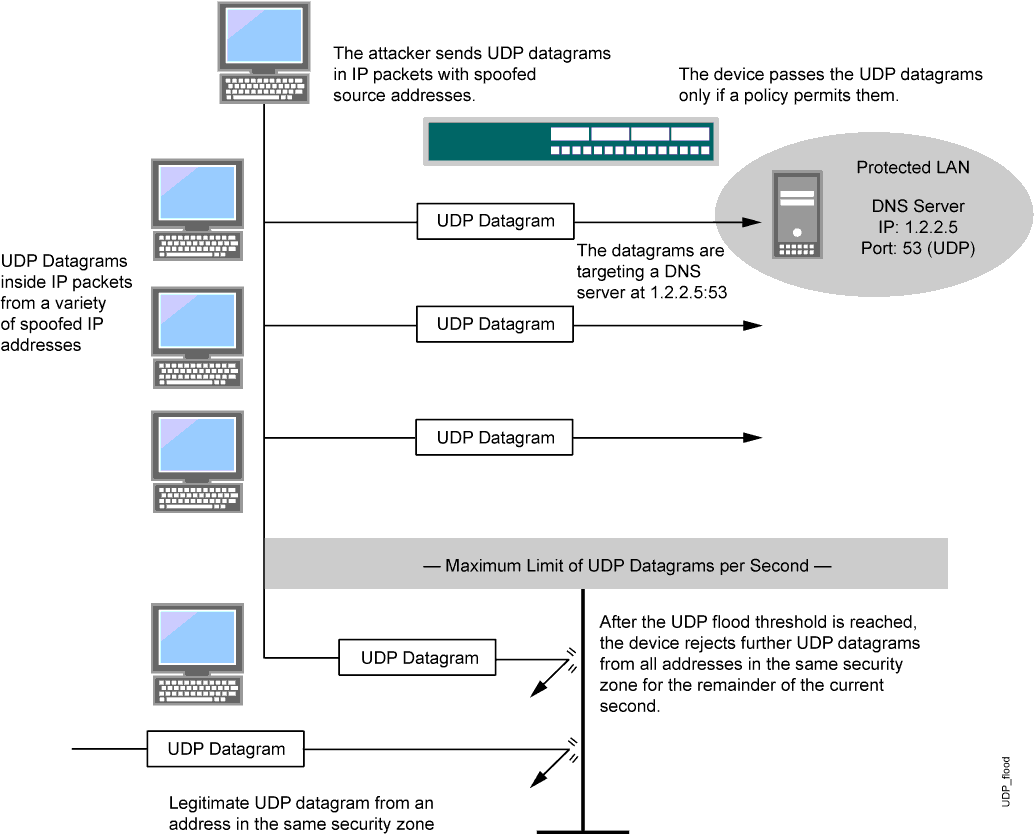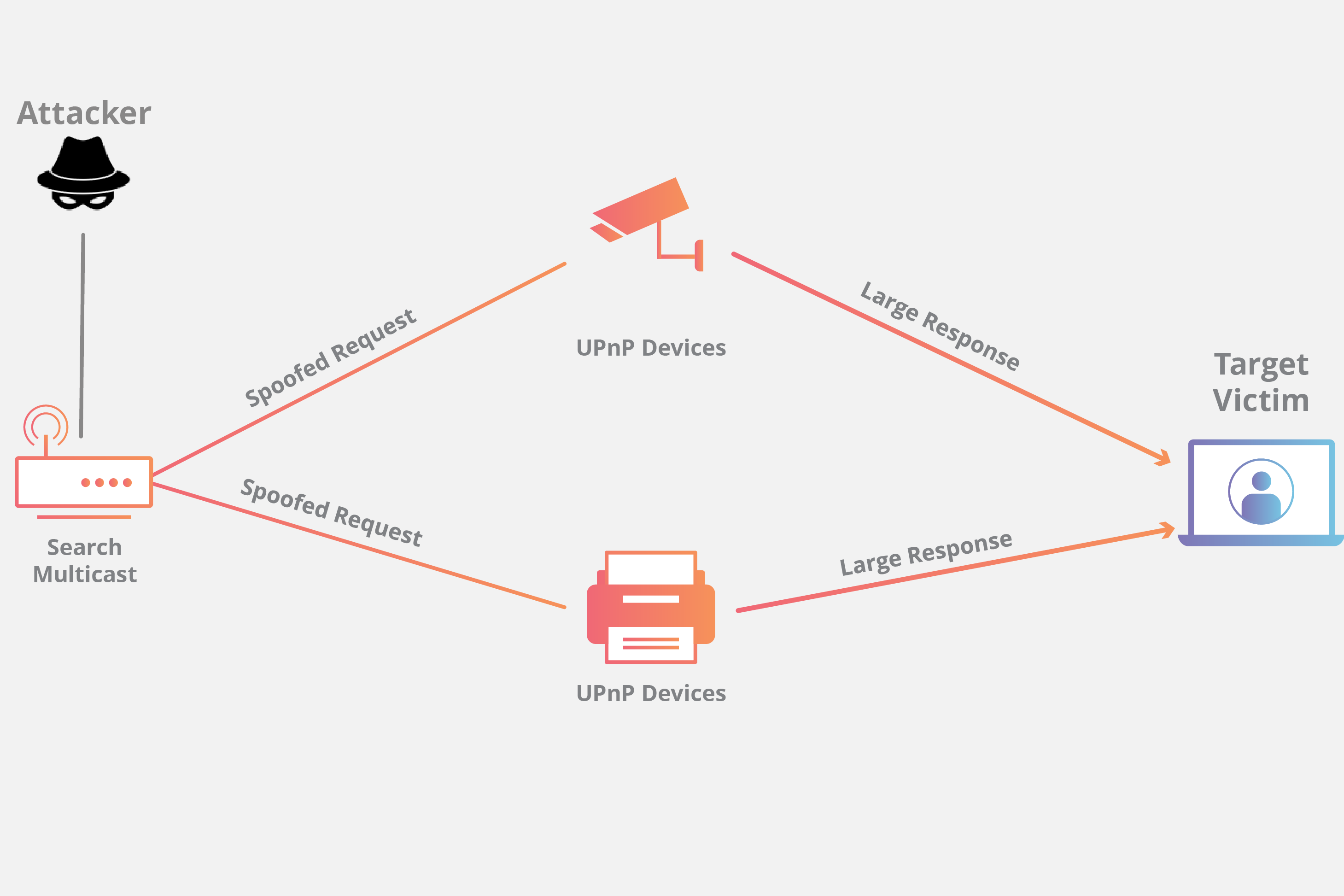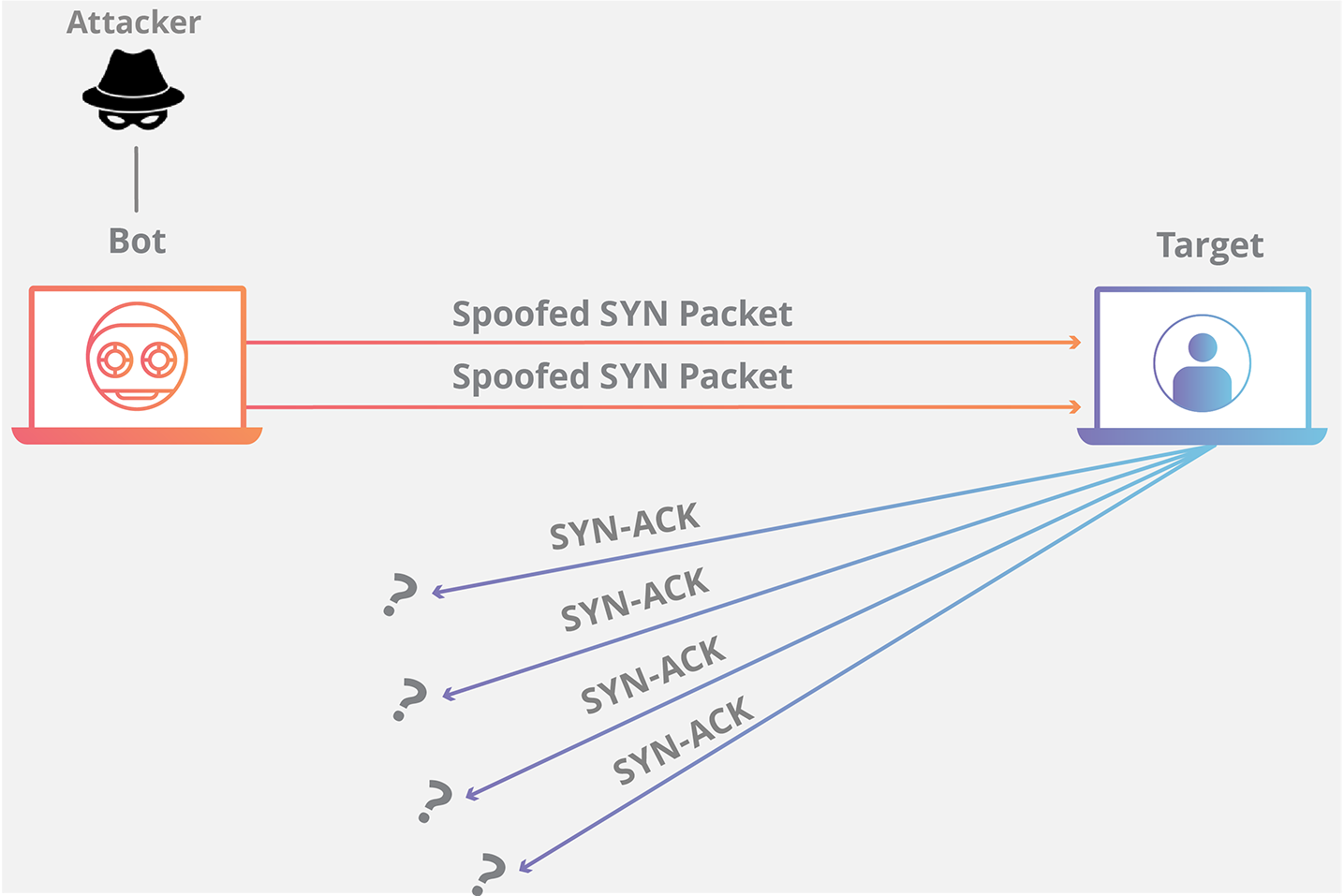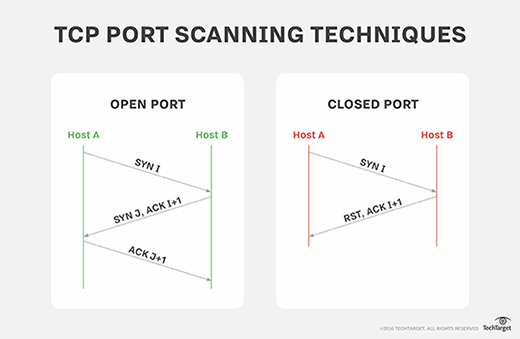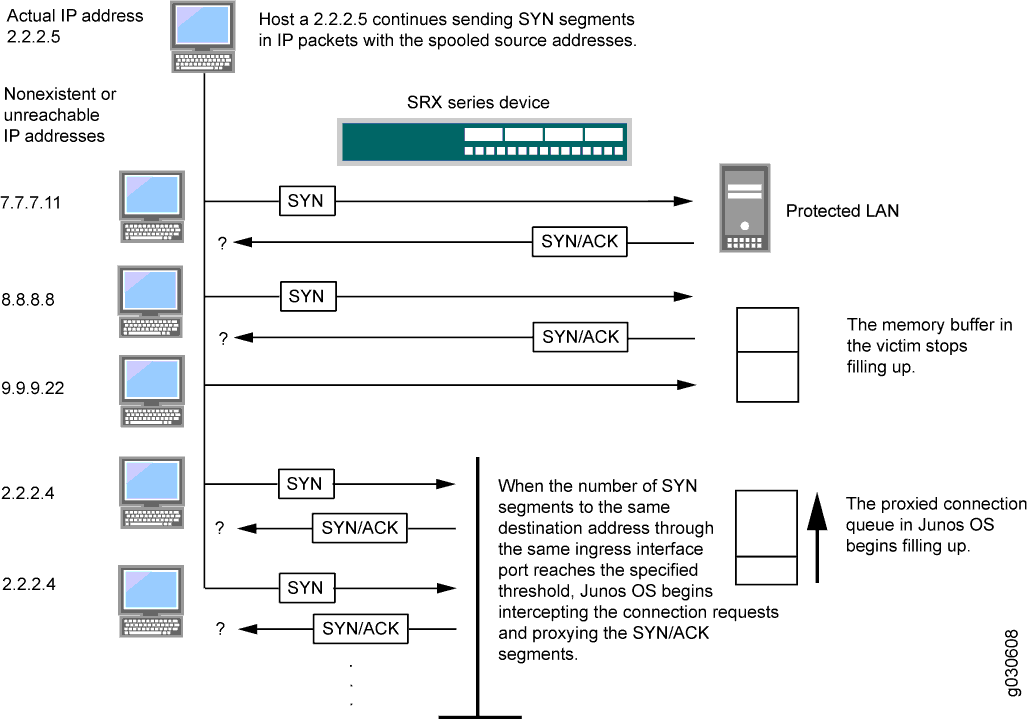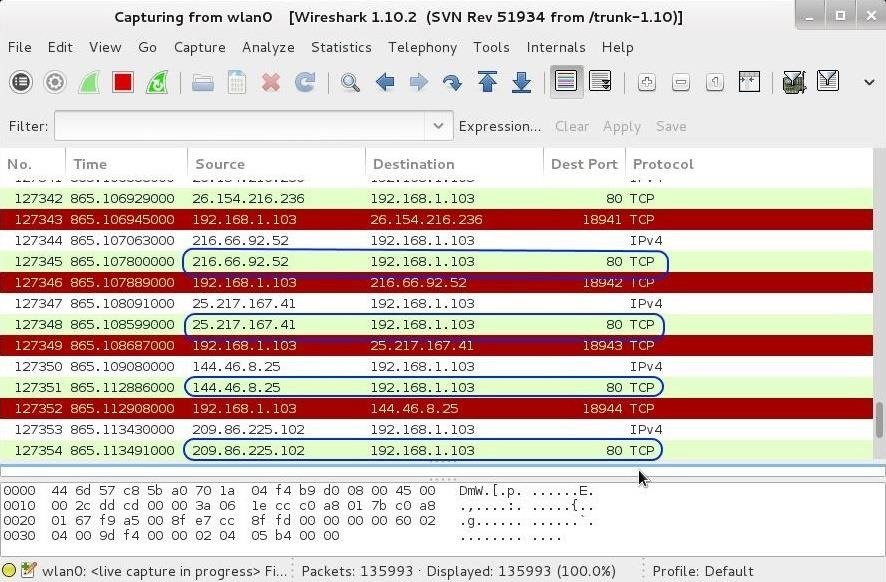
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 10 (Identifying Signatures of a Port Scan & DoS Attack) « Null Byte :: WonderHowTo

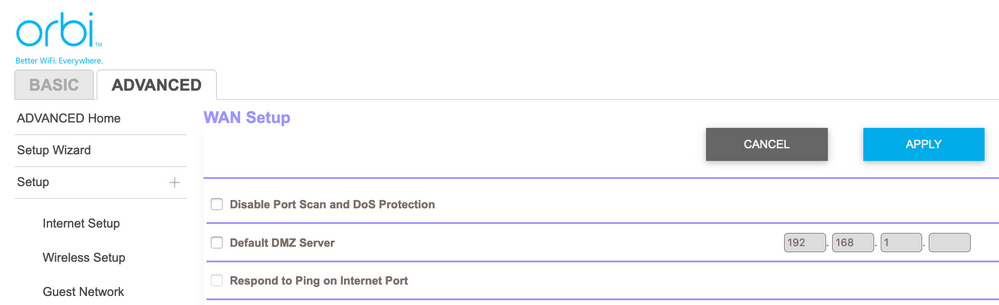
DOS Attack Ack Scan: What To Do When Your Router Logs It & How To Prevent One In The Future - One Computer Guy

Port scan attack successfully blocked through P4. Fig. 5: Scalability... | Download Scientific Diagram
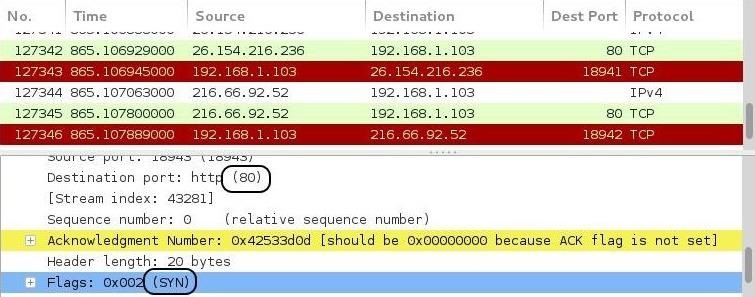
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 10 (Identifying Signatures of a Port Scan & DoS Attack) « Null Byte :: WonderHowTo